Profiles¶
What is a profile?¶
A profile is a set of data and various fingerprints collected from real computers. Our product uses this data to create a realistic browser fingerprint. Each profile also has an isolated repository for cookies, local storage, history, passwords and other settings.
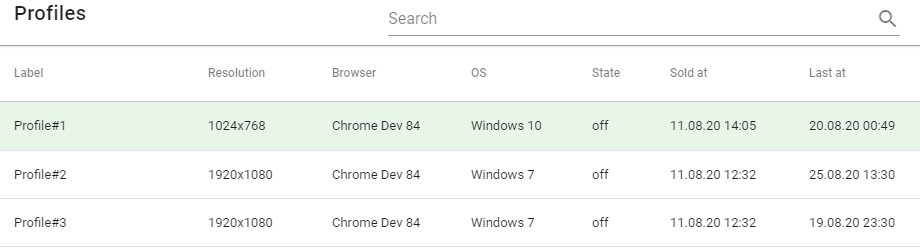
The Profiles section provides a table showing previously purchased profiles. In order to launch the browser with the profile you want, you need to do the following steps:
- Select the profile you are interested in (move your mouse over the line that describes the profile)
- Click on it.
- Enter settings in the Settings dialog box.
- In the upper right corner of the dialog box click on SAVE & RUN.
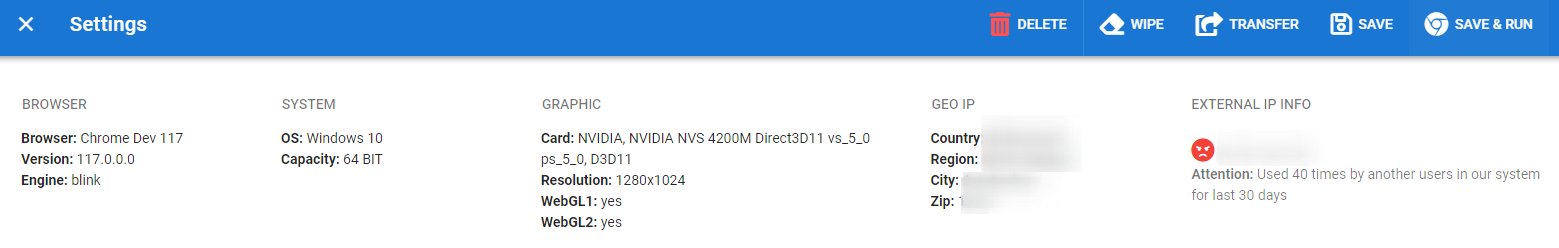
Information Block¶
This block contains the profile summary data. Some of the data changes dynamically, and some is static. The screenshot below shows an example of what this block looks like:
General Block¶
Profile Label¶
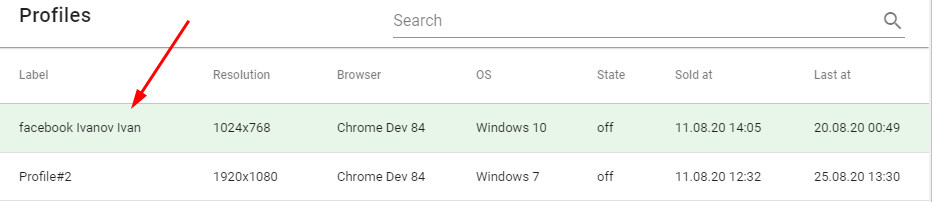
In the Profile label field, you can enter a name that symbolizes what the profile is for. This name will be displayed in the table with the list of your profiles. In the name, we recommend specifying a service. For example: facebook Ivanov Ivan. The service name in the profile name is recommended for easier sorting and searching.

After you save your profile, the name you need will be displayed in the general list:
Connection Settings¶
Two connection types are currently supported:
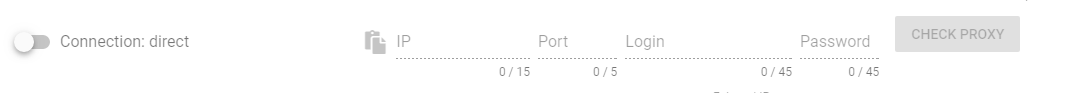
- direct - direct connection, without using a proxy:
- SOCKS5 proxy - connection via socks5 proxy:
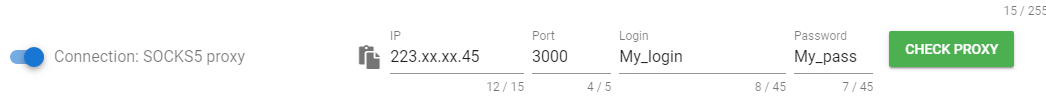
You should perform the following actions if you want to activate the socks5 proxy connection:
- Click on the radio button next to the word Connection. You will see that the connection type has changed from direct to SOCKS5 proxy. The IP, Port, Login, Password and CHECK PROXY button will be active.
- Enter data in the IP, Port, Login, Password fields.
- Click the CHECK PROXY button. The application will test if the SOCKS5 proxy you specified works. It will determine the external IP address and display it in the External IP field. It will detect Country, Region, City, Zip and display it in the corresponding information fields (in the upper block). If there are errors during proxy testing, the application will display this information in red. This information will be located under the Connection switch and duplicated in the upper block.
If you want to use a direct connection, just click on the switch next to the word Connection. The connection type will be changed from Connection: SOCKS5 proxy to Connection: direct. At the same time the application will display:
- in the External IP info field it will display your external IP address.
- the Country, Region, City, Zip information fields will display the data corresponding to your external IP address.
Geo Location Settings¶
The Geo location swap has two modes:
Geo location: original.
In this mode, the spoofing is not performed. And the geolocation data remains unchanged. In this case, the browser returns the real data. It looks like this:

Geo location: fake
This mode allows you to fake your geolocation data. When the spoofing mode is activated you can manually enter the latitude and longitude in the corresponding Latitude and Longitude fields. If you click on the SET AUTO button next to the latitude and longitude fields, the application will automatically fill these fields with the data corresponding to the external IP address. The value of this external IP address is specified in the External IP field. It looks like this:

Tip
Timezone & Language Settings¶
After obtaining the external IP address data, the SET AUTO button becomes active. This button is located next to the Timezone and Language fields. If you click on this button, the time zone and language will receive the values which were automatically determined for your external IP address.
Tip
You should understand and be aware of the moment when you need to configure or reconfigure the timezone and language. Usually this is done when you use the profile for the first time and remains unchanged afterwards.Many sites analyze this data. These sites may be very suspicious about changing this data. In practice, the average user very rarely changes this data. When you click on SET AUTO, the timezone and language will become the ones to which the IP belongs.
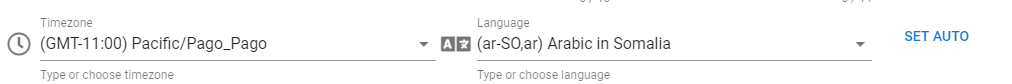
WebRTC Settings¶
Several types of spoofing and blocking IP detection via WebRTC are implemented:
- default: spoofing and blocking IP detection via WebRTC is disabled. But if the site uses WebRTC, you will see a message about it.
- fake: allows you to spoof the external IP address returned by the TUN server. The spoofing is done by hijacking the WebRTC API functions at the browser level. At the network level, WebRTC requests to the TUN server bypass the socks5 proxy. This is a standard implementation in the Chrome browser because WebRTC works over UDP. Chrome is able to proxy WebRTC requests through the socks5 proxy. But most socks5 proxy vendors simply do not support UDP over socks5. For this reason we have to perform substitution at browser level instead of at network level. See below for more details on how WebRTC spoofing works.
- block: completely disables WebRTC functionality.
What is WebRTC and how spoofing is implemented? WebRTC works over the UDP protocol. Although the standard describes that it can work with TCP, but in practice it is mainly used with UDP.
WebRTC is designed to connect two browsers directly without using a server in the middle. But in most cases users are behind a NAT router. I.e. there can be tens/hundreds/thousands of users behind one public IP. TUN servers are used to bypass the NAT and establish a direct connection from browser to browser. Here is a description of how NAT traversal through TUN servers works https://ru.wikipedia.org/wiki/STUN.
Tip
When browsers have made connections to a TUN server, they can establish a p2p (direct connection) to each other bypassing a third point. Even if both clients are behind a NAT router.
Almost all socks5 proxy providers provide proxies that support only TCP. Therefore we cannot proxy UDP. For this reason, the connection to the TUN server bypasses the proxy directly. If the proxy server does not support UDP, in this case it is technically impossible to implement WebRTC proxying.
IP detection via WebRTC is performed precisely at the stage of connection and communication between the browser and the TUN server. If WebRTC:fake is checked, then the TUN server response is spoofed at the level of the extension. That is, the TUN server returns your real IP (for example, your VPN), and the extension substitutes this IP for the desired one. The site when trying to get a response from the TUN-server (to get the external IP from the response) receives a tweaked response with the changed socks5 proxy IP instead of the real external IP.
When we analyzed the code of several antifraud solutions, we found that these solutions use their own TUN servers, not public ones. Obviously, these antifraud solutions also analyze requests on the TUN server side. For this reason, simply replacing the external IP address in the response of the TUN server at the extension level will have a negative effect, rather than the desired one.
For such situations, you can try one of the following options:
- Use VPN rather than socks5 proxy and disable WebRTC spoofing altogether (set WebRTC:default). For the reason that the VPN tunnels TCP and UDP, the TUN server will receive the external IP of your VPN.
- Block WebRTC completely (set WebRTC:block).
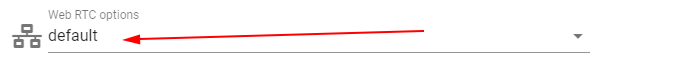
Customizations Block¶
This block displays active customizations in the current profile. The customizations are purchased simultaneously with the purchase of the profile through the store. The current example shows two active customizations for this profile - amazon and bestbuy.
Tip
Options Block¶
This block allows you to set a little more settings, if necessary. For example, you can set browser startup parameters, time shifting, cookie management and so on.
Browser CLI Params¶
Clicking this button opens a modal window in which you can specify command line parameters for the browser. Please specify each parameter on a new line - one parameter per line.
--param1--param2--param3--param1 --param2 --param3You can check the list of current parameters here https://peter.sh/experiments/chromium-command-line-switches. Note that the list of actual parameters may change with each release of Chrome.
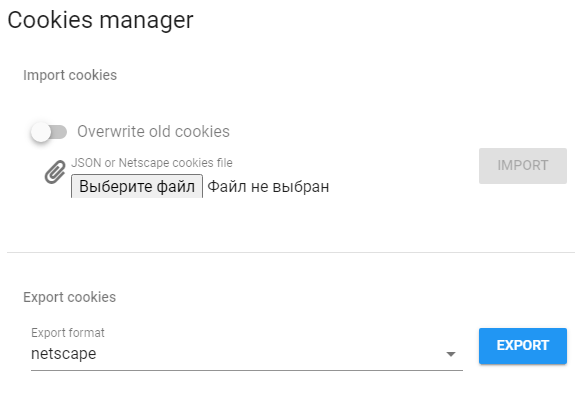
Cookies Manager¶
Clicking on this button opens a modal window in which you can import or export cookies for the current profile.
Two import and export formats are supported:
- JSON
- Netscape
Note that it is possible to overwrite existing cookies or update their values when importing. By default, existing cookie values will be updated. If, however, you want the old cookies to be completely removed before importing the new ones, then set the switch to Delete old cookies:
Tip
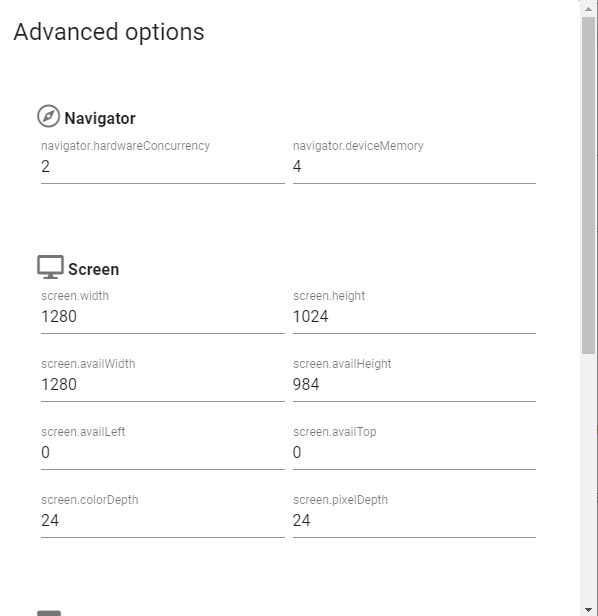
Advanced Options¶
The Advanced Options button allows you to fine-tune your profile after purchase.
Tip
In this box you can change the following settings:
- Browser version
- CPU
- Memory capacity
- Window Configuration
- Color depth
- Viewport size
You can also change other browser settings:
Time shifting¶
Time Shifting is several powerful technologies that allow you to control the time profile:
- reducing the resolution (frequency) of internal chromium timers
- stretching time between measurements
It’s no secret that almost all major sites pay close attention to timing of certain actions or functions when collecting browser fingerprints. The timing profile is a pretty broad topic, but here are a few examples:
- Measuring the time between keystrokes on the keyboard when filling out a form
- timing of mouse movements from point A to point B
- measuring time of execution of some javascript code
The above mentioned time profile techniques are not the only ones, there are also other more complicated and sophisticated ones. But the point boils down to one thing - it’s to calculate that the actions happen from the same computer or by the same person. Time Shifting allows you to influence and change time profiles in all their manifestations.
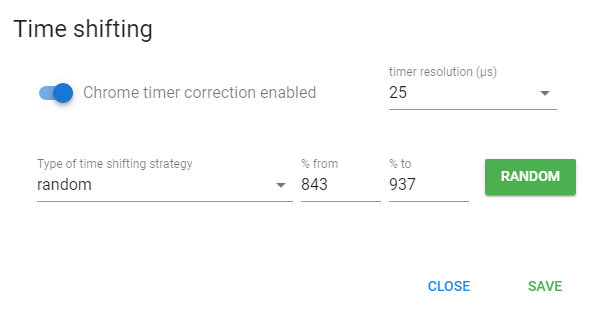
To enable the function that decreases the resolution (frequency) of the internal chromium timers, you should enable the Chrome timer correction checkbox and set the timer resolution (μs) value in the range from 5 to 5000 microseconds.
- default value for chromium/chrome is 5μs
- default value for firefox: 1000μs
You are free to try any of the values between 5 and 5000 μs and find the one which will work for your site. What specific values to set at a particular site can be calculated empirically. This will vary greatly from site to site, but we recommend that you try from 1000μs.
Select one of the available strategies to enable the time stretching function between measurements:
- off - disabled
- static - static value in percents. It increases the time delta between measurements.
- random - dynamic value in percent from the specified range. It increases the time delta between measurements.
Note that random strategy changes the value each time the page is refreshed. The range of valid values: 0 - 10000%.
In static strategy you can also specify the percentage value you are interested in, by which the time delta should be stretched during measurements. The range of possible values: 0 - 10000%. This strategy sets a static value and does not change with every page refresh.
WARNING. Don’t set the same or very close values on all profiles in a row. This may lead to negative results. Try to set different values on different profiles, differing by tens or even hundreds of percent. The exact limits depend on the site, but we recommend that the maximum should not exceed 300-500%.
Tip
Feature Block¶
In this block you can:
- control the emulation of the resolution swap. Two modes are available: simple and native.
- Manage the local port scanning ban feature.
- manage the DNS cache.
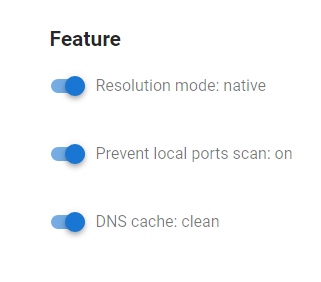
Emulation of Resolution¶
Simple mode. This emulates the desired resolution by swapping the properties of the window and screen javascript objects. In simple mode, the real viewport is visible. The size of the real viewport is detected in the following way: in the full screen browser window using HTML and Javascript an element div is created with the specified dimensions: “height:100%” and “width:100%”. Then its actual size in pixels is measured and the site determines the viewport value, which may not correspond to the actual physical resolution of the user’s monitor. In the vast majority of sites the viewport size is not detected and only the window and screen sizes are checked. At the moment we recommend to use simple mode.
Native mode. This is the emulation of the desired resolution through the implementation in the rendering mechanisms of the browser itself, up to the substitution of values returned by WinApi functions. In this mode, a problem arises when the emulated resolution is higher than the user’s real monitor resolution. In this case, the contents of the browser window must scroll not only vertically, but also horizontally, which leads to unnecessary keyboard and/or mouse clicks. This mode seems to us as the most “correct” from the antidetection point of view. Instructions for horizontal page scrolling at high resolutions in Native swap mode
Prevent local port scan¶
This option allows you to prevent sites from scanning open ports on your system. The scanning is done using WebSockets technology. For example, ebay.com scans the list of ports responsible for services related to remote desktop management: RDP, VNC, Team Viewer, etc. If you activate the “Prevent local port scan” option, Che Browser will catch the site’s attempts to scan and return information to the site that the port being scanned is closed.
Tip
This option is available in the profile settings in the Feature block:
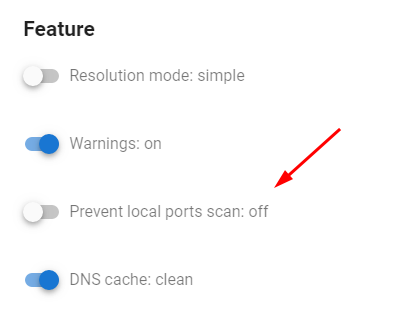
There are two modes available:
Prevent local ports scan: off - prevention of scanning is off (default browser behavior). When scanning, the site will be able to detect open ports.
Prevent local ports scan: on - scan prevention is enabled. When scanning, the site will not see open ports.
DNS cache cleaner¶
DNS Cache Cleanup is a simple, yet effective mechanism to prevent tracking based on storing the system/user ID in the DNS cache.
There are 2 modes available:
- leave: DNS cache remains unchanged and site will be able to detect two profiles
- clean: clear DNS cache before using a profile
Keep in mind that the DNS cache is shared by all applications within the OS. If you reset the DNS cache when using a profile, it will also be reset for active sessions.
About the principle of tracking when using the DNS cache.
There are several methods of such tracking, but the idea is that the DNS cache stores the user/system ID. When cookies, browser cache, local storage, etc. are cleared, the user/system ID can be recovered using DNS.
The DNS cache is layered. This means that the cache is not only stored on your PC, but and/or
- On your router
- At your ISP
- On the DNS servers that your ISP has given you
- and even on any server that makes a DNS query from you.
For this reason, you should understand that even if you have cleared your local DNS cache, it does not guarantee that the user/system ID will not be restored from the DNS cache from other servers of your DNS query.
In Che Browser, when using the socks5 proxy, domain resolution is performed on the socks5 proxy side. If you use a separate socks5 proxy for each profile and clear the local DNS cache, it becomes impossible to restore the user/system ID.
In any case, if you work with a site that uses such a method of tracking and do not use socks5 proxy, we strongly recommend you not to work with that site using 2 or more profiles simultaneously. This is necessary because the local DNS cache is common for the whole system. You should work with this site one by one from different profiles. I.e. having worked with the site from one profile, close the browser and then start the browser (with another profile) with the local DNS cache cleaning enabled.
Notice Field¶
In this field you can store some notes about the current profile. It is located at the bottom of the profile.

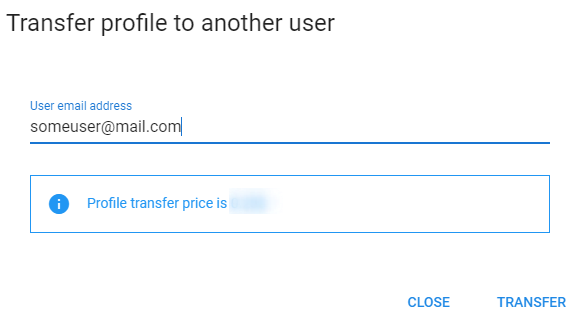
Transfer Button¶
This button is located in the upper right corner of the Settings Dialog Box. Since version 0.3, you can transfer a profile to another user. The window looks something like this:
Tip
WIPE Button¶
This button is located in the upper right corner of the Settings Dialog Box. If you click this button, then all user data is cleared, such as cookies, localstorage, history, etc.
Warning
DELETE Button¶
This button is located in the upper right corner of the Settings Dialog Box. Clicking this button deletes the profile irretrievably.
Warning
SAVE Button¶
This button is located in the upper right corner of the Settings Dialog Box. Clicking this button will save the profile settings you specified. Note that the settings you save do not apply to an already running session.
SAVE & RUN Button¶
This button is located in the upper right corner of the Settings Dialog Box. If you click it, you will save the profile settings and start the browser with these settings. Keep in mind that this button may not be active if the browser with this profile is already running.